Cyber Security Awareness
.jpg)
Never give out your username or password to anyone.If you think your computer may be compromised, contact our 24/7 OTS Service Desk right away at 832.813.6600. Were happy to help.
Think you may have received a phishing or scam email? Report it to the OTS Service Desk. Go to LSC Service Center > Communications and Collaboration > Email and use the "Report a Phishing/Scam Email" form to report a suspicious email received in your LSC email inbox.
Don't be a target for cyber-criminals
You may not realize it, but you are a target for cyber-criminals. Your computer, your mobile devices, your accounts, and your information all have tremendous value. The list below details many different ways in which cyber-criminals can make money by hacking you. Fortunately, by taking some simple steps, you can help protect yourself and your family.
Username & Passwords
Once hacked, cyber-criminals can install programs on your computer that capture all of your keystrokes, including your username and password. That information is used to log into your online accounts, such as:
Your bank or financial accounts, where they can steal or transfer your money
Your iCloud, Google Drive, or Dropbox account, where they can access all of your sensitive data
Your Amazon, WalMart or other online shopping accounts, where they can purchase goods in your name
Your UPS ore FedEx accounts, where they can ship stolen goods in your name

Email Harvesting
Once hacked, cyber-criminals can read your email for information they can sell to others, such as:
All the names, email addresses, and phone numbers from your contact list
All of your personal or work email
Virtual Goods
Once hacked, cyber-criminals can copy and steal any virtual goods you have and sell them to others, such as:
Your online gaming characters, gaming goods, or gaming currencies
Any software licenses, operating system license keys, or gaming licenses
Botnet
Once hacked, your computer can be connected to an entire network of hacked computers controlled by the cyber-criminal. This network, called botnet, can then be used for activities such as:
Sending out spam to millions of people
Launching Denial of Service attacks
Identity Hijacking
Once hacked, cyber-criminals can steal your online identity to commit fraud or sell your identity to others, such as:
Your Facebook, Twitter, or LinkedIn account
Your email accounts
Your Skype or other IM accounts

Web Server
Once hacked, cyber-criminals can turn your computer into a web server, which they can then use for the following:
Host phishing websites to steal other peoples usernames and passwords
Host attacking tools that will hack peoples computers
Distribute child pornography, pirated videos, or stolen music
Financial
Once hacked, cyber-criminals can scan your system looking for valuable information, such as:
Your credit card information
Your tax records and past filings
Your financial investments and retirement plans
Extortion
Once hacked, cyber-criminals can take over your computer and demand money. They do this by:
Taking pictures of your with your computers camera and demanding payment to destroy or not release the pictures
Encrypting all the data on your computer and demanding payment to decrypt it
Tracking all websites you visit and threatening to publish them

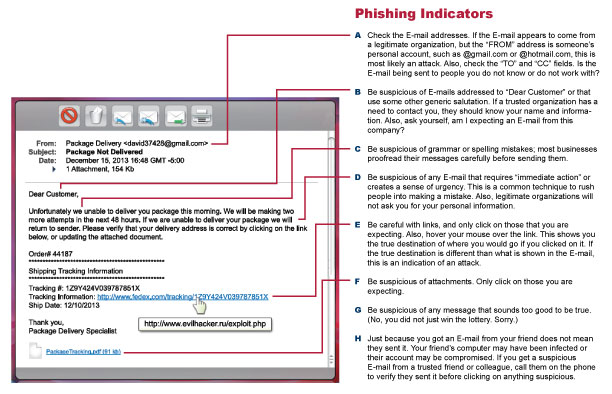
Phishing
Phishing is a psychological attack used by cyber-criminals to trick you into giving up information or taking an action. Phishing originally described email attacks that would steal your online username and password. However, the term has evolved and now refers to almost any message-based attack. These attacks begin with a cyber-criminal sending a message pretending to be from someone or something you know, such as a friend, your bank or a well-known store or website.
These message entice you into taking an action, such as clicking on a malicious link, opening an infected attachment, or responding to a scam. Cyber-criminals craft these convincing-looking emails and send them to millions of people around the world. The criminals do not know who will fall victim, they simply know that the more emails they send out, the more people they will have the opportunity to hack. In addition, cyber-criminals are not limited to just email but will use other methods, such as instant messaging or social media posts.
Spear Phishing
The concept is the same as phishing, except that instead of sending random emails to millions of potential victims, cyber-attackers send targeted messages to a very few select individuals. With spear phishing, the cyber-attackers research their intended targets, such as by reading the Intended victim's LinkedIn or Facebook accounts or any messages they have posted on public blogs or forums. Based on this research, the attackers then create a highly-customized email that appears relevant to the intended targets. This way, the individuals are far more likely to fall victim.
The cyber-criminal information presented above is based on the original work of Brian Krebs. You can learn more about cyber-criminals at his blog at: http://krebsonsecurity.com.
LSC is a National Cyber-Security Awareness Month Champion
Lone Star College is a recognized NCSAM Champion by the National Cyber Security Alliance. Visit stopthinkconnect.org for tips & advice. Every October, OTS observes National Cyber Security Awareness Month (NCSAM) to help raise awareness among students, faculty, staff about ways we can all be safe and secure online. No one person, company, or agency is responsible for the security of the Internet. Cyber security is our shared responsibility, and we all play a part in keeping data safe.
.gif)
Throughout the month of October, National Cyber Security Awareness Month, OTS sends weekly email blasts with helpful tips and reminders to our faculty, staff and students on topics such as what to do if you spot "phishy" emails and how to keep from getting locked out of your account when it comes time to change your network password. In addition to the helpful information in the weekly emails, OTS runs digital signage across the campuses throughout the month that offers tips on keeping data safe and how to be responsible online. The Awareness Program is intended to educate the campus community on information security topics, to heighten awareness regarding information security, and to reduce the risks of a security breach.
A Cyber Security Awareness Bulletin is sent to students weekly, and to faculty and staff at regular intervals, throughout the year with similar cyber security topics to help keep them informed year-round.
